.netcore-.NET Core 实现 JWT 认证
推荐 原创写在前面
JWT(JSON Web Token)是一种开放标准, 由三部分组成,分别是Header、Payload和Signature,它以 JSON 对象的方式在各方之间安全地传输信息。通俗的说,就是通过数字签名算法生产一个字符串,然后在网络请求的中被携带到服务端进行身份认证,功能上来说和 SessionId 认证方式很像。
在.Net Core 中使用JWT 可以通过 NuGet 获取 Microsoft.AspNetCore.Authentication.JwtBearer 包。

另外JWT需要配置一个Key, 需要提前生成好;在上一篇中介绍过:
用keytool 生成JWT的RSA非对称密钥-CSDN博客
代码实现
appsettings.json 中的配置
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft.AspNetCore": "Warning"
}
},
"AllowedHosts": "*",
"Jwt": {
"Key": "MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEArLhdR+Df8J9jNN4xuF9eqtbmibTpLaj1Re/e2aCuCFtVTfDgKsHklSSC4O8Jq0cyEBKs/SGhP8DD3w9vgFuWbpUcoYsWAEaV0zjWtJtng+upcpa4VTgi2jLltht+ukTs3f5uUsAXQT8pbBLyBZEcKZ1AuvFZCasG6BYPOJSiypQIeCWo0nq4u3cyaX4C5qjdhacxtT7RVXtQ5nWnMQxP+Mq2mf5x/zWEcCDhPFM5w7ulkcGOoWSCA3lRMOFB7fX49shBLgKAkATsSEB+EtmpWdbyI1pbRMqteWPELMLEB8EuJ0IEI4LRC59rlh/aQYHmyZnAKR", // 密钥
"Issuer": "rjcql", // 颁发者
"Audience": "rjcql" // 接收者
}
}
代码主体:
using Microsoft.AspNetCore.Authentication.JwtBearer;
using Microsoft.AspNetCore.Authorization;
using Microsoft.IdentityModel.Tokens;
using System.IdentityModel.Tokens.Jwt;
using System.Security.Claims;
using System.Text;
var builder = WebApplication.CreateBuilder(args);
builder.Services.AddAuthentication(options =>
{
options.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultScheme = JwtBearerDefaults.AuthenticationScheme;
}).AddJwtBearer(o =>
{
o.TokenValidationParameters = new TokenValidationParameters
{
ValidIssuer = builder.Configuration["Jwt:Issuer"],
ValidAudience = builder.Configuration["Jwt:Audience"],
IssuerSigningKey = new SymmetricSecurityKey
(Encoding.UTF8.GetBytes(builder.Configuration["Jwt:Key"])),
ValidateIssuer = true,
ValidateAudience = true,
ValidateLifetime = false,
ValidateIssuerSigningKey = true
};
});
builder.Services.AddAuthorization();
var app = builder.Build();
app.UseHttpsRedirection();
app.MapGet("/", () => "Hello everyone.");
app.MapGet("/security/getMessage", () => "Hello rjcql!").RequireAuthorization();
app.MapPost("/security/createToken",
[AllowAnonymous] (User user) =>
{
if (user.UserName == "rjcql" && user.Password == "111111")
{
var issuer = builder.Configuration["Jwt:Issuer"];
var audience = builder.Configuration["Jwt:Audience"];
var key = Encoding.ASCII.GetBytes
(builder.Configuration["Jwt:Key"]);
var tokenDescriptor = new SecurityTokenDescriptor
{
Subject = new ClaimsIdentity(new[]
{
new Claim("Id", Guid.NewGuid().ToString()),
new Claim(JwtRegisteredClaimNames.Sub, user.UserName),
new Claim(JwtRegisteredClaimNames.Email, user.UserName),
new Claim(JwtRegisteredClaimNames.Jti,
Guid.NewGuid().ToString())
}),
Expires = DateTime.UtcNow.AddMinutes(5),
Issuer = issuer,
Audience = audience,
SigningCredentials = new SigningCredentials
(new SymmetricSecurityKey(key),
SecurityAlgorithms.HmacSha512Signature)
};
var tokenHandler = new JwtSecurityTokenHandler();
var token = tokenHandler.CreateToken(tokenDescriptor);
var jwtToken = tokenHandler.WriteToken(token);
var stringToken = tokenHandler.WriteToken(token);
return Results.Ok(stringToken);
}
return Results.Unauthorized();
});
app.UseAuthentication();
app.UseAuthorization();
app.Run();
public class User
{
public string UserName { get; set; }
public string Password { get; set; }
}调用示例
运行站点

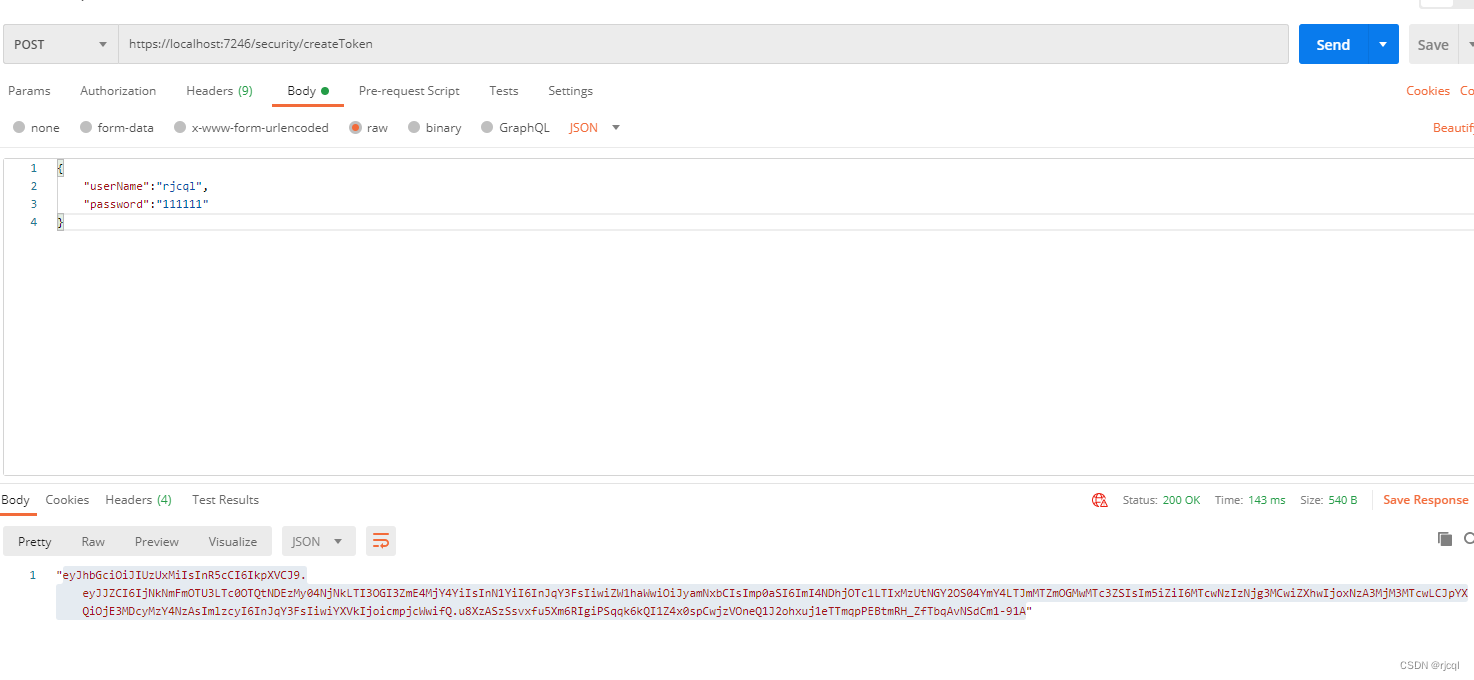
用postman获取token
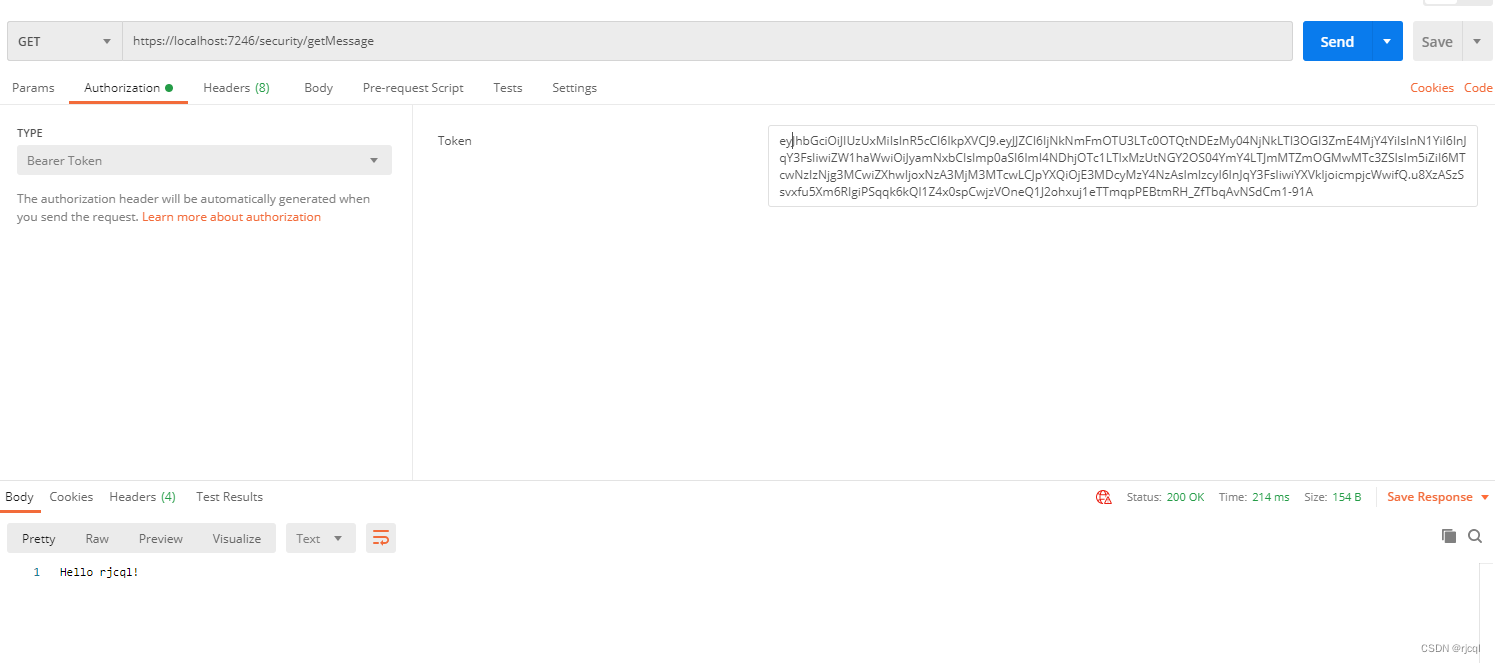
使用token访问目标链接
更多【.netcore-.NET Core 实现 JWT 认证】相关视频教程:www.yxfzedu.com
相关文章推荐
- 学习-Retrieval-Augmented Generation for Knowledge-Intensive NLP Tasks - 翻译学习 - 其他
- python-第三章:人工智能深度学习教程-基础神经网络(第四节-从头开始的具有前向和反向传播的深度神经网络 – Python) - 其他
- css-数据结构与算法 | 第四章:字符串 - 其他
- 编程技术-自媒体项目详述 - 其他
- aac-FFMPEG库实现mp4/flv文件(H264+AAC)的封装与分离 - 其他
- jvm-设计模式详解(十)——装饰器模式 - 其他
- hive-C++自动注册的工厂与--whole-archive - 其他
- 编程技术-C语言基础篇3:函数 - 其他
- java-Java 实现视频Mov转Mp4 - 其他
- 编程技术-强化学习中蒙特卡罗方法 - 其他
- 机器学习-使用深度神经网络预测股票价格 - 其他
- c#-C# OpenCvSharp DNN HybridNets 同时处理车辆检测、可驾驶区域分割、车道线分割 - 其他
- 小程序-小程序发成绩 - 其他
- 前端-使用Nodejs搭建简单的Web网页并实现公网访问 - 其他
- jvm-JVM在线分析-监控工具(jps, jstat, jstatd) - 其他
- 交友-如何设计开发一对一交友App吸引更多活跃用户 - 其他
- 学习-深度学习/pytoch/pycharm学习过程中遇到的问题 - 其他
- jvm-在GORM中使用并发 - 其他
- aws-aws亚马逊:什么是 Amazon EC2? - 其他
- aws-aws亚马逊云:置以使用 Amazon EC2!!! - 其他
记录自己的技术轨迹
文章规则:
1):文章标题请尽量与文章内容相符
2):严禁色情、血腥、暴力
3):严禁发布任何形式的广告贴
4):严禁发表关于中国的政治类话题
5):严格遵守中国互联网法律法规
6):有侵权,疑问可发邮件至service@yxfzedu.com
近期原创 更多
