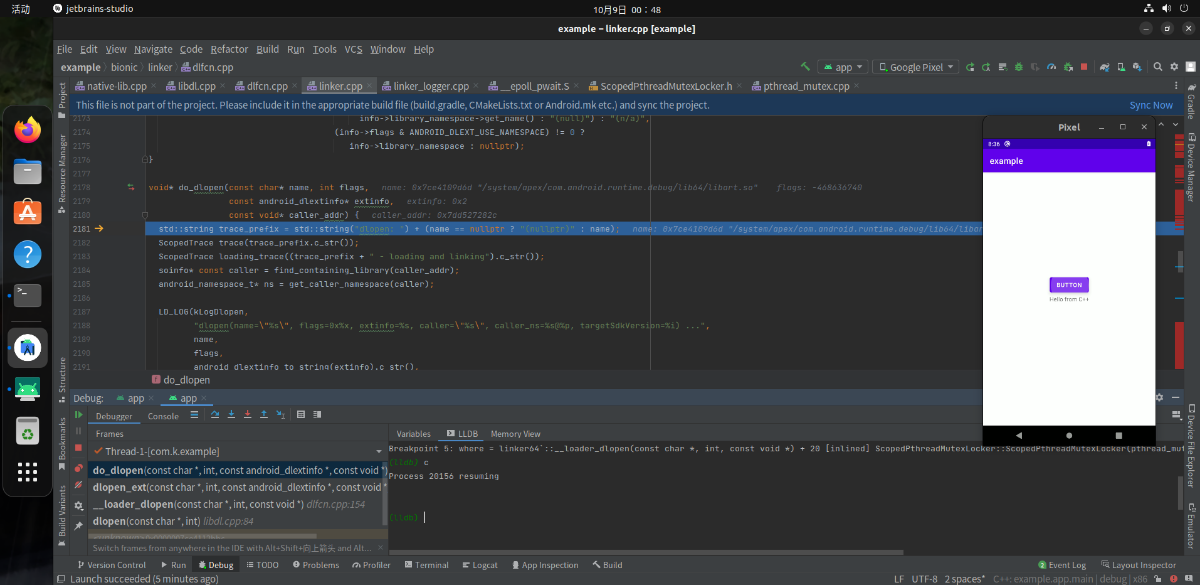
k@k:~
/
bin
/
aosp
/
out
/
target
/
product
/
sailfish
/
symbols
/
apex
/
com.android.runtime.debug
/
bin
$ readelf
-
S linker64
There are
30
section headers, starting at offset
0x11c0f00
:
节头:
[号] 名称 类型 地址 偏移量 大小 全体大小 旗标 链接 信息 对齐
[
0
] NULL
0000000000000000
00000000
0000000000000000
0000000000000000
0
0
0
[
1
] .note.gnu.bu[...] NOTE
0000000000000238
00000238
0000000000000020
0000000000000000
A
0
0
4
[
2
] .dynsym DYNSYM
0000000000000258
00000258
0000000000000240
0000000000000018
A
4
1
8
[
3
] .gnu.
hash
GNU_HASH
0000000000000498
00000498
00000000000000c0
0000000000000000
A
2
0
8
[
4
] .dynstr STRTAB
0000000000000558
00000558
00000000000002b2
0000000000000000
A
0
0
1
[
5
] .relr.dyn LOOS
+
0xfffff00
0000000000000810
00000810
00000000000001f0
0000000000000008
A
0
0
8
[
6
] .rodata PROGBITS
0000000000000a00
00000a00
0000000000017d0d
0000000000000000
AMS
0
0
32
[
7
] .gcc_except_table PROGBITS
0000000000018710
00018710
00000000000050dc
0000000000000000
A
0
0
4
[
8
] .eh_frame_hdr PROGBITS
000000000001d7ec
0001d7ec
0000000000004bc4
0000000000000000
A
0
0
4
[
9
] .eh_frame PROGBITS
00000000000223b0
000223b0
0000000000014f24
0000000000000000
A
0
0
8
[
10
] .text PROGBITS
0000000000038000
00038000
00000000000d1528
0000000000000000
AX
0
0
64
[
11
] .data PROGBITS
000000000010a000
0010a000
0000000000000ef8
0000000000000000
WA
0
0
32
[
12
] .data.rel.ro PROGBITS
000000000010b000
0010b000
0000000000006270
0000000000000000
WA
0
0
8
[
13
] .init_array INIT_ARRAY
0000000000111270
00111270
0000000000000060
0000000000000008
WA
0
0
8
[
14
] .dynamic DYNAMIC
00000000001112d0
001112d0
00000000000000e0
0000000000000010
WA
4
0
8
[
15
] .got PROGBITS
00000000001113b0
001113b0
0000000000000820
0000000000000000
WA
0
0
8
[
16
] .bss NOBITS
0000000000112000
00111bd0
0000000000009e70
0000000000000000
WA
0
0
4096
[
17
] .debug_str PROGBITS
0000000000000000
00111bd0
00000000003ae347
0000000000000001
MS
0
0
1
[
18
] .debug_loc PROGBITS
0000000000000000
004bff17
00000000003f6b1c
0000000000000000
0
0
1
[
19
] .debug_abbrev PROGBITS
0000000000000000
008b6a33
000000000003f6ae
0000000000000000
0
0
1
[
20
] .debug_info PROGBITS
0000000000000000
008f60e1
00000000006391f2
0000000000000000
0
0
1
[
21
] .debug_ranges PROGBITS
0000000000000000
00f2f2d3
00000000000ed620
0000000000000000
0
0
1
[
22
] .debug_macinfo PROGBITS
0000000000000000
0101c8f3
0000000000000164
0000000000000000
0
0
1
[
23
] .comment PROGBITS
0000000000000000
0101ca57
000000000000019c
0000000000000001
MS
0
0
1
[
24
] .debug_line PROGBITS
0000000000000000
0101cbf3
000000000011cb4a
0000000000000000
0
0
1
[
25
] .debug_aranges PROGBITS
0000000000000000
0113973d
00000000000013e0
0000000000000000
0
0
1
[
26
] .gnu_debuglink PROGBITS
0000000000000000
0113ab1d
0000000000000020
0000000000000000
0
0
1
[
27
] .shstrtab STRTAB
0000000000000000
011c0dbe
000000000000013c
0000000000000000
0
0
1
[
28
] .symtab SYMTAB
0000000000000000
0113ab40
00000000000484b0
0000000000000018
29
12315
8
[
29
] .strtab STRTAB
0000000000000000
01182ff0
000000000003ddce
0000000000000000
0
0
1
Key to Flags:
W (write), A (alloc), X (execute), M (merge), S (strings), I (info),
L (link order), O (extra OS processing required), G (group), T (TLS),
C (compressed), x (unknown), o (OS specific), E (exclude),
k@k:~
/
bin
/
aosp
/
out
/
target
/
product
/
sailfish
/
symbols
/
apex
/
com.android.runtime.debug
/
bin
$ ll
-
hr|grep linker64
-
rwxrwxr
-
x
1
k k
18M
10
月
8
01
:
09
linker64
*