登陆 / 注册
重置密码
首页 文章 CTF对抗 某手游xqtd的简单分析
某手游xqtd的简单分析
推荐 原创闲着没事,看到有新游出来,于是简单的分析学习一下。
由于时间和水平有限,本文会存在诸多不足,欢迎补充指正。
样本:xqtd
加固:mtp
工具:ida、010、jadx、frida
libtprt.so简单处理
寄存器间接跳转
第一种,流程很清晰,比较好处理
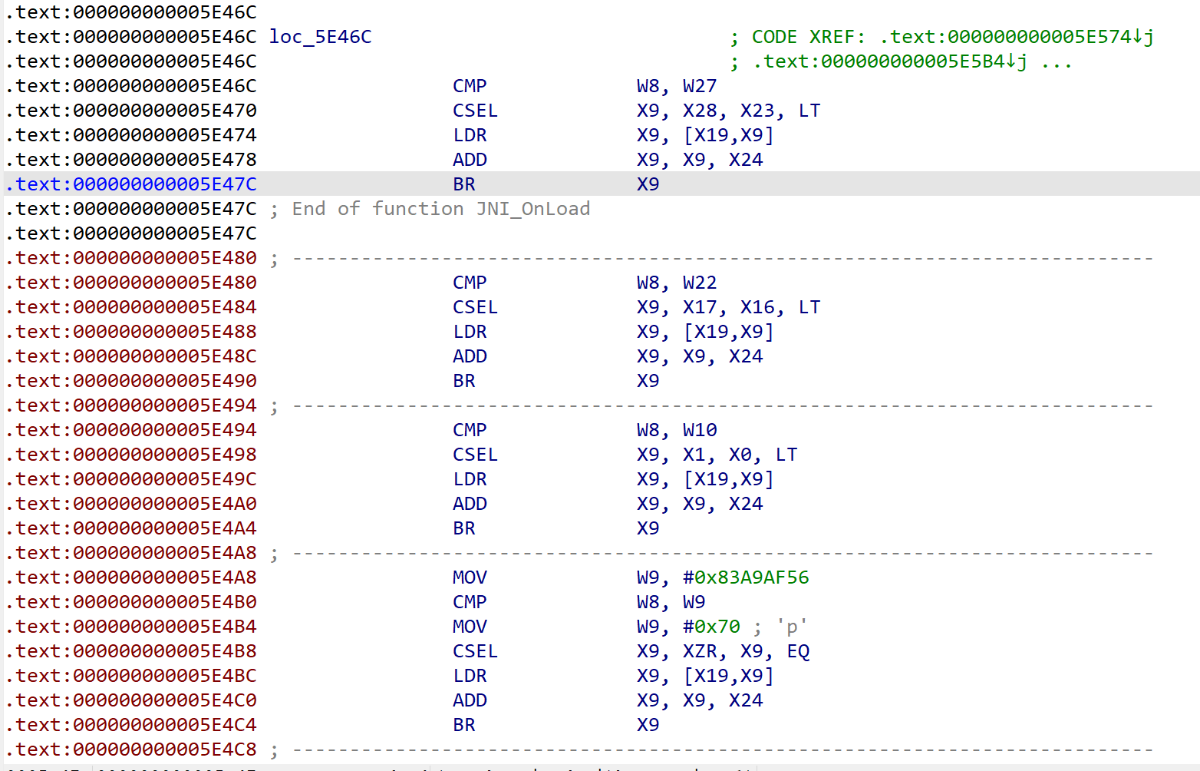
ida脚本,如遇到报错需要修改脚本
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
|
import
idautils
import
idc
import
idaapi
import
ida_ua
from
keystone
import
*
g_reg
=
[
0
]
*
40
reg_base
=
129
g_cond_info
=
list
()
ldr_reg
=
-
1
add_reg
=
-
1
ks
=
keystone.Ks(keystone.KS_ARCH_ARM64, keystone.KS_MODE_LITTLE_ENDIAN)
def
get_opcode(ea):
opcode
=
None
disasm
=
idc.GetDisasm(ea)
if
disasm.find(
'LT'
) !
=
-
1
:
opcode
=
'blt'
elif
disasm.find(
'EQ'
) !
=
-
1
:
opcode
=
'beq'
elif
disasm.find(
'CC'
) !
=
-
1
:
opcode
=
'bcc'
elif
disasm.find(
'GT'
) !
=
-
1
:
opcode
=
'bgt'
elif
disasm.find(
'NE'
) !
=
-
1
:
opcode
=
'bne'
elif
disasm.find(
'GE'
) !
=
-
1
:
opcode
=
'bge'
elif
disasm.find(
'HI'
) !
=
-
1
:
opcode
=
'bhi'
return
opcode
def
do_patch(patch_1, patch_2, opcode, cond_jmp_addr, uncond_jmp_addr):
print
(
"patch_1=0x%x patch_1=0x%x opcode=%s cond_jmp_addr=0x%x uncond_jmp_addr=0x%x"
%
(patch_1, patch_2, opcode, cond_jmp_addr, uncond_jmp_addr))
jump_offset
=
" ({:d})"
.
format
(cond_jmp_addr
-
patch_1)
repair_opcode
=
opcode
+
jump_offset
encoding, count
=
ks.asm(repair_opcode)
idaapi.patch_byte(patch_1, encoding[
0
])
idaapi.patch_byte(patch_1
+
1
, encoding[
1
])
idaapi.patch_byte(patch_1
+
2
, encoding[
2
])
idaapi.patch_byte(patch_1
+
3
, encoding[
3
])
jump_offset
=
" ({:d})"
.
format
(uncond_jmp_addr
-
patch_2)
repair_opcode
=
'b'
+
jump_offset
encoding, count
=
ks.asm(repair_opcode)
idaapi.patch_byte(patch_2, encoding[
0
])
idaapi.patch_byte(patch_2
+
1
, encoding[
1
])
idaapi.patch_byte(patch_2
+
2
, encoding[
2
])
idaapi.patch_byte(patch_2
+
3
, encoding[
3
])
def
do_deobf(ea):
# 获取跳转条件
opcode
=
get_opcode(ea)
if
opcode
is
None
:
print
(
"opcode:unknown opcode 0x%x"
%
ea)
return
ea
# 获取跳转信息
cond_reg
=
-
1
uncond_reg
=
-
1
cond_data
=
-
1
uncond_data
=
-
1
mnem
=
idc.ida_ua.ua_mnem(ea)
if
mnem
=
=
'CSEL'
:
cond_reg
=
idc.get_operand_value(ea,
1
)
uncond_reg
=
idc.get_operand_value(ea,
2
)
elif
mnem
=
=
'CSET'
:
cond_data
=
1
uncond_data
=
0
ea
=
idc.next_head(ea)
# 获取LDR寄存器
ldr_reg
=
-
1
lsl_value
=
-
1
mnem
=
idc.ida_ua.ua_mnem(ea)
if
mnem
=
=
'LSL'
:
lsl_value
=
idc.get_operand_value(ea,
2
)
ea
=
idc.next_head(ea)
mnem
=
idc.ida_ua.ua_mnem(ea)
if
mnem !
=
'LDR'
:
print
(
"LDR:0x%x -> %s"
%
(ea, mnem))
return
ea
operand_type
=
idc.get_operand_type(ea,
1
)
if
operand_type
=
=
idc.o_phrase:
insn
=
ida_ua.insn_t()
ida_ua.decode_insn(insn, ea)
ldr_reg
=
insn.Op2.reg
if
lsl_value
=
=
-
1
:
lsl_value
=
insn.Op2.value
else
:
return
ea
ea
=
idc.next_head(ea)
# 获取ADD寄存器
mnem
=
idc.ida_ua.ua_mnem(ea)
if
mnem
=
=
'MOV'
:
ea
=
idc.next_head(ea)
mnem
=
idc.ida_ua.ua_mnem(ea)
if
mnem !
=
'ADD'
:
print
(
"ADD:0x%x -> %s"
%
(ea, mnem))
return
ea
op_3
=
idc.print_operand(ea,
2
)
op_3
=
op_3[
1
:]
ea
=
idc.next_head(ea)
# 进行patch
mnem
=
idc.ida_ua.ua_mnem(ea)
if
mnem !
=
'BR'
:
print
(
"BR:0x%x -> %s"
%
(ea, mnem))
return
ea
#print('1 = %d 2 = %d 3 = 0x%x' % (g_reg[ldr_reg - reg_base], g_reg[cond_reg - reg_base], g_reg[int(op_3)]))
if
cond_data !
=
-
1
and
uncond_data !
=
-
1
:
print
(lsl_value)
cond_jmp_addr
=
(idc.get_qword(g_reg[ldr_reg
-
reg_base]
+
(cond_data << lsl_value))
+
g_reg[
int
(op_3)]) &
0xffffffffffffffff
uncond_jmp_addr
=
(idc.get_qword(g_reg[ldr_reg
-
reg_base]
+
(uncond_data << lsl_value))
+
g_reg[
int
(op_3)]) &
0xffffffffffffffff
else
:
cond_jmp_addr
=
(idc.get_qword(g_reg[ldr_reg
-
reg_base]
+
(g_reg[cond_reg
-
reg_base] << lsl_value))
+
g_reg[
int
(op_3)]) &
0xffffffffffffffff
uncond_jmp_addr
=
(idc.get_qword(g_reg[ldr_reg
-
reg_base]
+
(g_reg[uncond_reg
-
reg_base] << lsl_value))
+
g_reg[
int
(op_3)]) &
0xffffffffffffffff
do_patch(idc.prev_head(ea), ea, opcode, cond_jmp_addr, uncond_jmp_addr)
return
ea
def
deobf(ea):
off_reg
=
-
1
off_data
=
-
1
while
True
:
mnem
=
idc.ida_ua.ua_mnem(ea)
if
mnem
=
=
'RET'
:
break
elif
mnem
=
=
'MOV'
:
op_1_type
=
idc.get_operand_type(ea,
0
)
op_2_type
=
idc.get_operand_type(ea,
1
)
if
(op_1_type
=
=
idc.o_reg)
and
(op_2_type
=
=
idc.o_imm):
op_1
=
idc.get_operand_value(ea,
0
)
op_2
=
idc.get_operand_value(ea,
1
)
g_reg[op_1
-
reg_base]
=
op_2
elif
mnem
=
=
'MOVK'
:
op_1_type
=
idc.get_operand_type(ea,
0
)
op_2_type
=
idc.get_operand_type(ea,
1
)
op_3_type
=
idc.get_operand_type(ea,
2
)
if
(op_1_type
=
=
idc.o_reg)
and
(op_2_type
=
=
idc.o_imm):
op_1
=
idc.get_operand_value(ea,
0
)
op_2
=
idc.get_operand_value(ea,
1
)
g_reg[op_1
-
reg_base]
=
(op_2 <<
16
) | (g_reg[op_1
-
reg_base] &
0xffff
)
elif
mnem
=
=
'ADRP'
:
op_1
=
idc.get_operand_value(ea,
0
)
op_2
=
idc.get_operand_value(ea,
1
)
off_reg
=
op_1
off_data
=
op_2
elif
mnem
=
=
'ADD'
:
op_1
=
idc.get_operand_value(ea,
0
)
op_2
=
idc.get_operand_value(ea,
1
)
op_3
=
idc.get_operand_value(ea,
2
)
op_3_type
=
idc.get_operand_type(ea,
2
)
if
(op_1
=
=
off_reg)
and
(op_2
=
=
off_reg)
and
(op_3_type
=
=
idc.o_imm):
off_data
=
off_data
+
op_3
ldr_reg
=
off_reg
-
reg_base
g_reg[ldr_reg]
=
off_data
elif
(mnem
=
=
'CSEL'
)
or
(mnem
=
=
'CSINC'
)
or
(mnem
=
=
'CSET'
)
or
(mnem
=
=
'CINC'
):
ea
=
do_deobf(ea)
continue
ea
=
idc.next_head(ea)
def
test():
for
i
in
range
(
len
(g_reg)):
print
(
"%d:0x%x"
%
(i, g_reg[i]))
def
main():
ea
=
idc.get_screen_ea()
func
=
idaapi.get_func(ea)
ea
=
func.start_ea
print
(
"start deobf fun:0x%x"
%
(ea))
deobf(ea)
print
(
"deobf ok!"
)
pass
if
__name__
=
=
"__main__"
:
main()
|
处理前
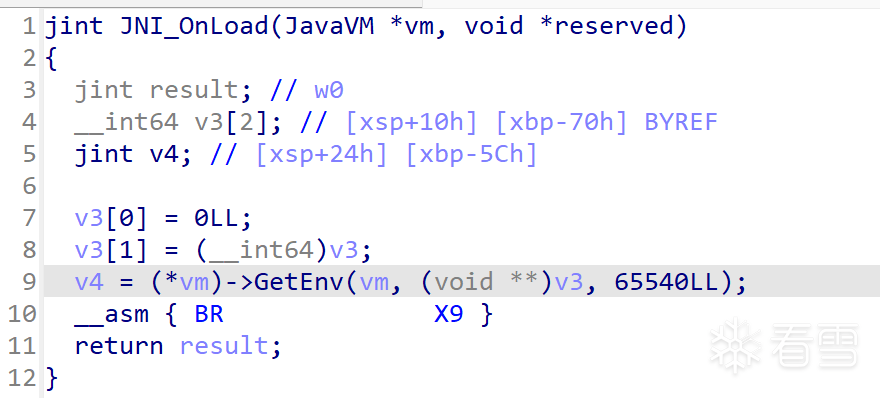
处理后
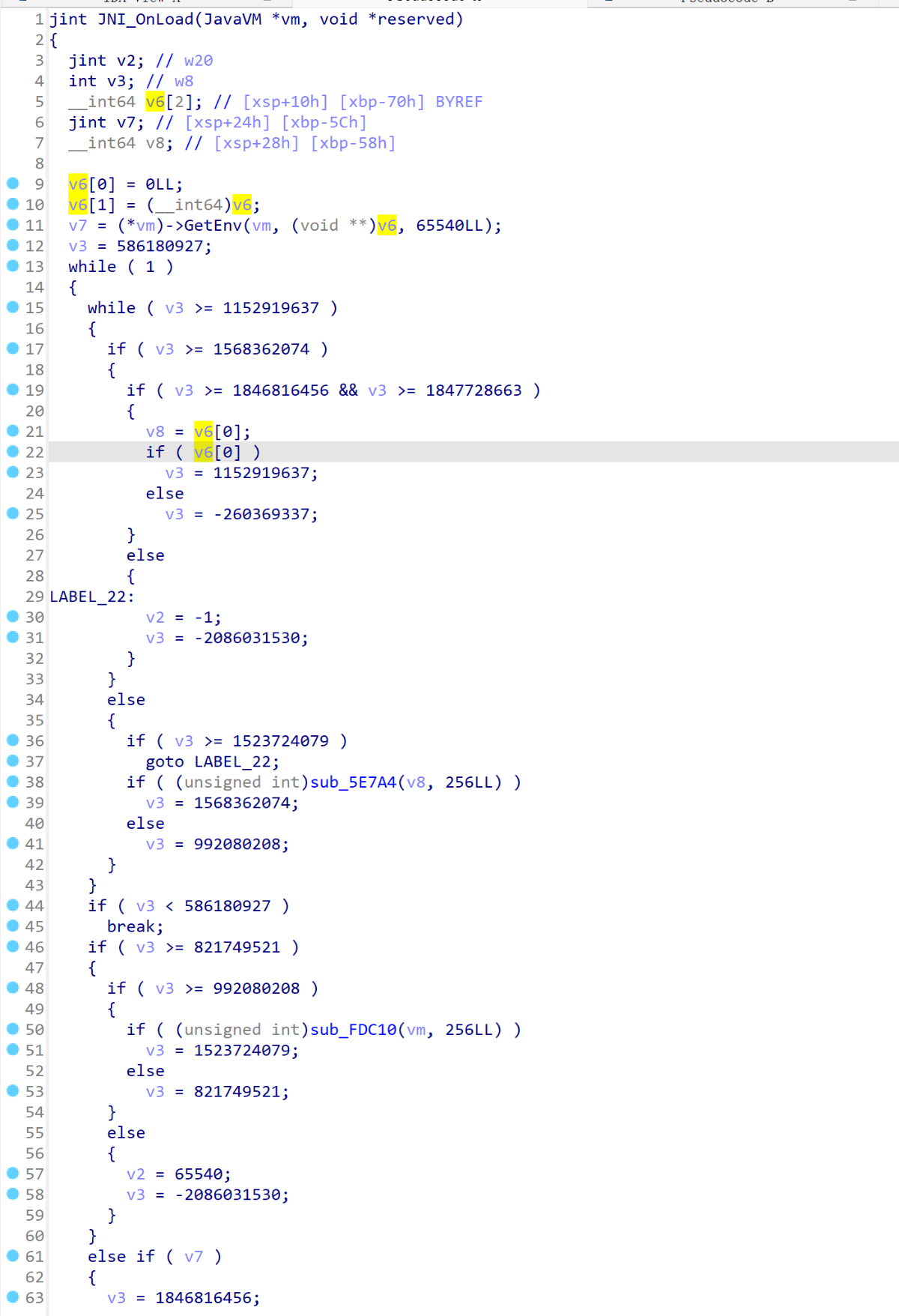
第二种,有点像做了流水线优化,不太好处理
- 观察发现存在这种间接跳转的方法,其方法的流程并不复杂,将各种跳转
patch掉即可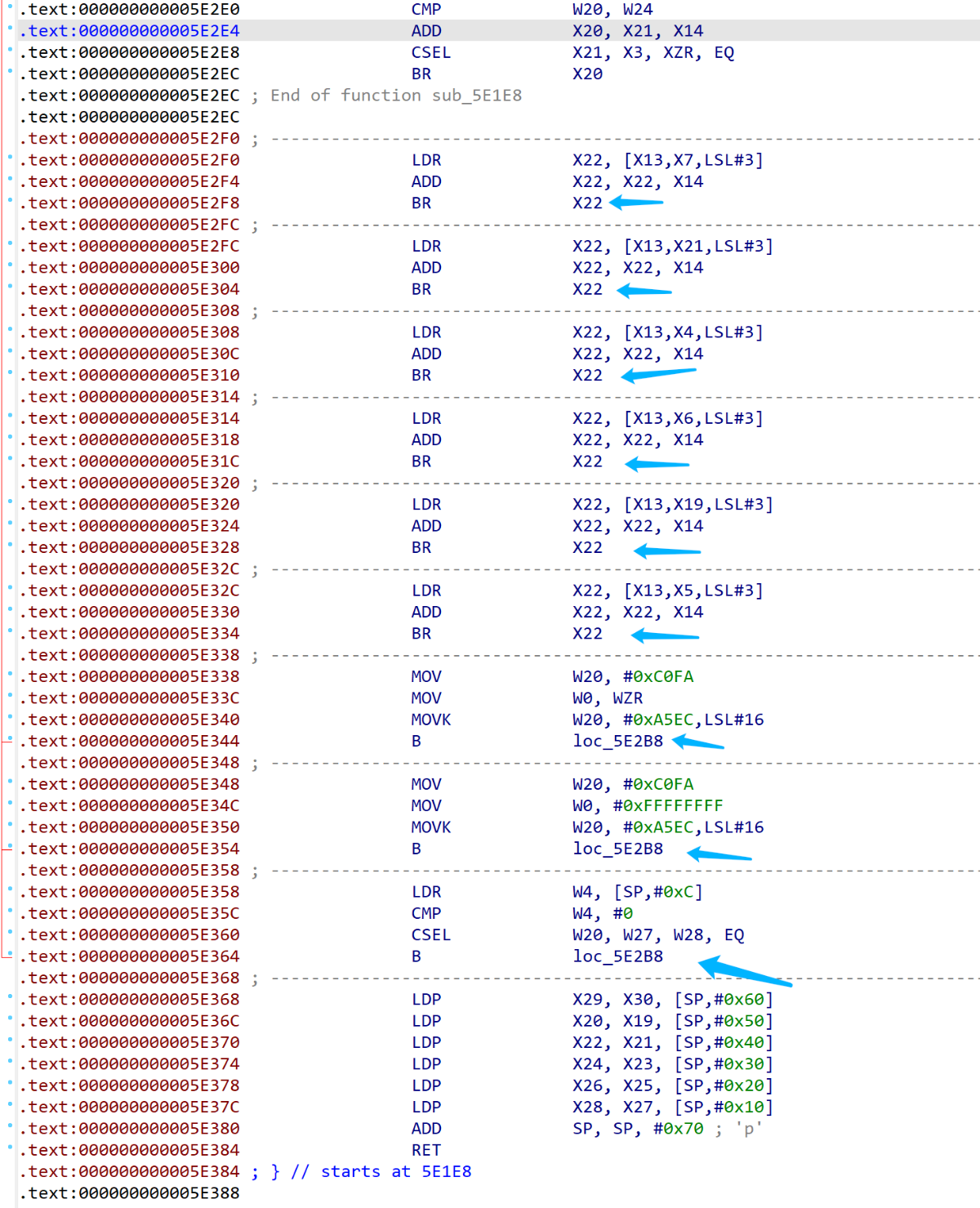
字符串解密
libtprt.so中,部分字符串的解密,都是同一个算法,写了个简单脚本libtersafe2.so中其实也是一样的
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
|
import
idautils
import
idc
import
idaapi
decrypt_fun_list
=
dict
()
def
get_code_refs_to_list(addr):
result
=
list
(idautils.CodeRefsTo(addr,
True
))
return
result
def
do_decrypt(src_addr, dst_addr, offset, eor_data, add_data, call_addr):
flag
=
idc.get_wide_byte(src_addr)
str_len
=
flag ^ (idc.get_wide_byte(src_addr
+
1
))
final_str
=
''
for
i
in
range
(str_len):
v4
=
idc.get_wide_byte(src_addr
+
2
+
i)
v5
=
(flag
+
i) ^ eor_data
final_str
+
=
chr
((v4 ^ flag) &
0xff
)
flag
=
v5
+
add_data
decrypt_fun_list[call_addr]
=
final_str
+
" "
+
str
(
hex
(offset))
print
(
'decrypt_addr=0x%x offset=0x%x, final_str=%s'
%
(call_addr, offset, final_str))
def
decrpt_str():
decrypt_fun_list.clear()
tmp_list
=
[
7
,
6
,
5
,
4
,
3
,
2
,
1
]
fun_list
=
get_code_refs_to_list(
0x106C54
)
if
not
fun_list:
return
for
i
in
range
(
len
(fun_list)):
call_addr
=
fun_list[i]
call_addr_start
=
idc.get_func_attr(call_addr, idc.FUNCATTR_START)
caller_fun_list
=
get_code_refs_to_list(call_addr_start)
for
j
in
range
(
len
(caller_fun_list)):
call_decryptStr_addr
=
caller_fun_list[j]
arg_addr
=
idc.prev_head(call_decryptStr_addr)
mnem
=
idc.ida_ua.ua_mnem(arg_addr)
register
=
idc.get_operand_value(arg_addr,
0
)
while
True
:
if
(register
=
=
129
)
and
(mnem
=
=
'MOV'
):
break
arg_addr
=
idc.prev_head(arg_addr)
mnem
=
idc.ida_ua.ua_mnem(arg_addr)
register
=
idc.get_operand_value(arg_addr,
0
)
offset
=
idc.get_operand_value(arg_addr,
1
)
if
offset
=
=
0xa0
:
offset
=
0
src_addr
=
0x1250D8
+
offset
dst_addr
=
0x15E778
+
offset
index
=
offset
%
100
eor_data
=
index
add_data
=
tmp_list[(index
%
7
)]
do_decrypt(src_addr, dst_addr, offset, eor_data, add_data, call_decryptStr_addr)
pass
def
main():
decrpt_str()
if
__name__
=
=
"__main__"
:
main()
|
- 解密结果,还是暴露了不少关键信息的
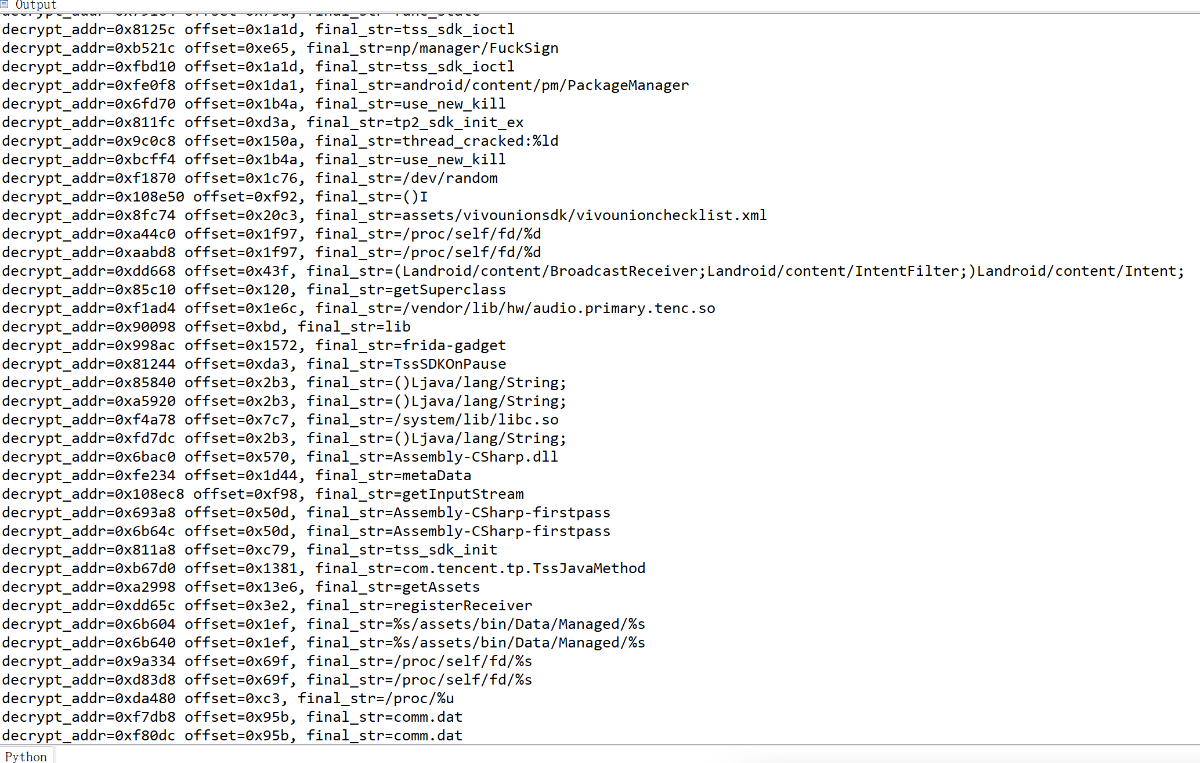
ollvm混淆
- 不算太严重,不是很影响分析,也就没有处理,将就着看了
libtprt.so检测
hook检测
- 在
0xB1484中会对代码段计算crc32并进行比较- 从
0x5e0f0到0x11fb90,大小0xc1aa0 - 修改返回结果为0来过掉检测
- 从
- 在
sub_9AAFC中获取linker64的路径,通过解析文件格式获取符号的地址- 在方法
sub_F5AC0:对文件中和内存中方法的前32个字节进行比较 - 获取的符号如下
- 在方法
|
1
2
3
|
__loader_dlopen
__loader_android_dlopen_ext
rtld_db_dlactivity
/
/
在非调试模式下为空函数,如果程序被调试则会被修改为对应的断点指令
|
- 在方法
sub_B4BC0反射调用来了findClass
|
1
2
3
4
|
cc
/
binmt
/
signature
/
PmsHookApplication
com
/
cloudinject
/
feature
/
App
np
/
manager
/
FuckSign
bin
/
mt
/
apksignaturekillerplus
/
HookApplication
|
emulator检测
- 在
sub_F19B0访问目标文件
|
1
2
3
4
5
6
|
/
init.vbox86.rc
/
dev
/
socket
/
genyd
/
data
/
data
/
com.tencent.tinput
init.android_x86.rc
ueventd.android_x86.rc
/
system
/
framework
/
x86
|
Seccomp-BPF检测
- 在
sub_AA338打开了/proc/self/status,获取了Seccomp对应的值 - 其中
sub_A9EB0方法返回值即Seccomp对应的值
debugger检测
- 在方法
sub_DCCE8反射获取ADB_ENABLED - 在方法
sub_DD468反射获取android.hardware.usb.action.USB_STATE - 在方法
sub_98B34遍历maps查找libjdwp.so 在方法
sub_985D4反射调用isDebuggerConnected在方法
sub_9843C使用socket连接了127.0.0.1:23946- 在方法
sub_F0DAC打开了/proc/%d/status,获取了TracerPid - 在方法
sub_9BE6C中创建了线程,并调用gettimeofday获取了线程创建前后的时间差
frida检测
在方法
sub_98B34遍历maps查找frida-gadget、frida-agent在方法
sub_994A8使用socket连接了127.0.0.1:27402
使用strong-frida编译修改的frida,需要修改对应的端口
同时,在frida中,将对应的hook检测过掉,就可以正常的对libtprt.so进行hook
libtersafe2.so的简单分析
字符串解密
- 和上面一样
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
|
import
idautils
import
idc
import
idaapi
decrypt_fun_list
=
dict
()
def
get_code_refs_to_list(addr):
result
=
list
(idautils.CodeRefsTo(addr,
True
))
return
result
def
do_decrypt(src_addr, dst_addr, offset, eor_data, add_data, call_addr):
flag
=
idc.get_wide_byte(src_addr)
str_len
=
flag ^ (idc.get_wide_byte(src_addr
+
1
))
final_str
=
''
for
i
in
range
(str_len):
v10
=
idc.get_wide_byte(src_addr
+
2
+
i) ^ flag
flag
=
((i
+
flag) ^ eor_data)
+
add_data
final_str
+
=
chr
(v10 &
0xff
)
decrypt_fun_list[call_addr]
=
final_str
+
" "
+
str
(
hex
(offset))
print
(
'call_addr=0x%x, offset=0x%x, eor_data=0x%x, add_data=0x%x, final_str=%s'
%
(call_addr, offset, eor_data, add_data, final_str))
def
decrpt_str():
decrypt_fun_list.clear()
tmp_list
=
[
7
,
6
,
5
,
4
,
3
,
2
,
1
]
fun_list
=
get_code_refs_to_list(
0x27E724
)
if
not
fun_list:
return
for
i
in
range
(
len
(fun_list)):
arg_addr
=
fun_list[i]
call_addr
=
arg_addr
fun_start
=
idc.get_func_attr(arg_addr, idc.FUNCATTR_START)
mnem
=
idc.ida_ua.ua_mnem(arg_addr)
register
=
idc.get_operand_value(arg_addr,
0
)
while
arg_addr >
=
fun_start:
if
(register
=
=
129
)
and
(mnem
=
=
'MOV'
):
offset
=
idc.get_operand_value(arg_addr,
1
)
break
arg_addr
=
idc.prev_head(arg_addr)
mnem
=
idc.ida_ua.ua_mnem(arg_addr)
register
=
idc.get_operand_value(arg_addr,
0
)
if
offset
=
=
0xa0
:
offset
=
0
index
=
offset
%
100
eor_data
=
index
add_data
=
tmp_list[(index
%
7
)]
# src = 0x3880E4 dst = 0x4C9B78
src_addr
=
0x3880E4
+
offset
dst_addr
=
0x4C9B78
+
offset
do_decrypt(src_addr, dst_addr, offset, eor_data, add_data, call_addr)
def
main():
decrpt_str()
if
__name__
=
=
"__main__"
:
main()
|
- 字符串暴露出了很多关键信息
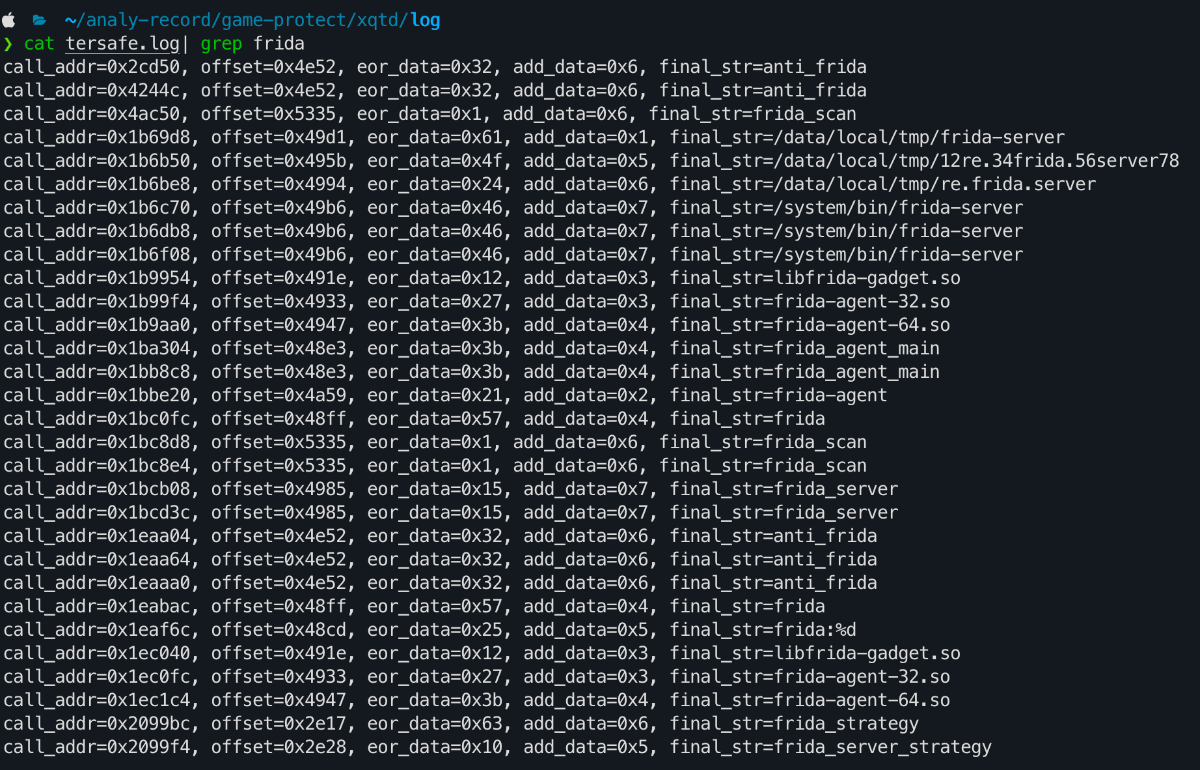
相关的检测和脚本
- 在方法
sub_26A218进行脚本方法的初始化
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
|
__int64 __fastcall sub_26A218(__int64 result)
{
v1
=
result;
if
( !
*
(_QWORD
*
)(result
+
8
) )
{
v11
=
sub_27E724(
0x1ADE
);
v12
=
0
;
v13[
0
]
=
(__int64)sub_26E5D8;
v13[
1
]
=
sub_27E724(
0x1AEB
);
v14
=
0
;
v15
=
sub_26E644;
v16
=
sub_27E724(
0x1AF9
);
v17
=
0
;
v18
=
sub_26E700;
v19
=
sub_27E724(
0x147E
);
v20
=
13
;
v21
=
sub_26B698;
v22
=
sub_27E724(
5260
);
v23
=
11
;
v24
=
sub_26B398;
v25
=
sub_27E724(
5266
);
v26
=
4
;
v27
=
sub_26B714;
v28
=
sub_27E724(
5276
);
v29
=
4
;
v30
=
sub_26B748;
v31
=
sub_27E724(
5286
);
v32
=
2
;
v33
=
sub_26B76C;
v34
=
sub_27E724(
5299
);
v35
=
3
;
v36
=
sub_26B79C;
v37
=
sub_27E724(
5312
);
v38
=
3
;
v39
=
&sub_26B824;
v40
=
sub_27E724(
5322
);
v41
=
14
;
v42
=
sub_26CC04;
v43
=
sub_27E724(
5330
);
v44
=
3
;
v45
=
&sub_26B8A0;
v46
=
sub_27E724(
5341
);
v47
=
3
;
v48
=
sub_26B918;
v49
=
sub_27E724(
5356
);
v50
=
5
;
v51
=
sub_26BB7C;
v52
=
sub_27E724(
5370
);
v53
=
3
;
v54
=
sub_26BACC;
v55
=
sub_27E724(
5384
);
v56
=
4
;
v57
=
sub_26BD10;
v58
=
sub_27E724(
5398
);
v59
=
4
;
v60
=
sub_26BDE8;
v61
=
sub_27E724(
5413
);
v62
=
5
;
v63
=
sub_26BEBC;
v64
=
sub_27E724(
5428
);
v65
=
5
;
v66
=
sub_26BF74;
v67
=
sub_27E724(
5443
);
v68
=
5
;
v69
=
sub_26C02C;
v70
=
sub_27E724(
5458
);
v71
=
2
;
v72
=
sub_26C0E4;
v73
=
sub_27E724(
5465
);
v74
=
3
;
v75
=
sub_26C128;
v76
=
sub_27E724(
5478
);
v77
=
3
;
v78
=
sub_26C208;
v79
=
sub_27E724(
5491
);
v80
=
3
;
v81
=
sub_26C1C8;
v82
=
sub_27E724(
5504
);
v83
=
3
;
v84
=
sub_26C248;
v85
=
sub_27E724(
5521
);
v86
=
3
;
v87
=
sub_26C288;
v88
=
sub_27E724(
5539
);
v89
=
3
;
v90
=
sub_26C338;
v91
=
sub_27E724(
5553
);
v92
=
3
;
v93
=
sub_26C3AC;
v94
=
sub_27E724(
5566
);
v95
=
3
;
v96
=
sub_26C45C;
v97
=
sub_27E724(
5579
);
v98
=
3
;
v99
=
sub_26C404;
v100
=
sub_27E724(
5592
);
v101
=
3
;
v102
=
sub_26B934;
v103
=
sub_27E724(
5605
);
v104
=
3
;
v105
=
sub_26B9BC;
v106
=
sub_27E724(
5618
);
v107
=
3
;
v108
=
sub_26BA44;
v109
=
sub_27E724(
5631
);
v110
=
17
;
v111
=
sub_26CC54;
v112
=
sub_27E724(
5645
);
v113
=
18
;
v114
=
sub_26CC98;
v115
=
sub_27E724(
5661
);
v116
=
19
;
v117
=
sub_26CCF4;
v118
=
sub_27E724(
5681
);
v119
=
15
;
v120
=
sub_26C4B4;
v121
=
sub_27E724(
5700
);
v122
=
20
;
v123
=
sub_26CD64;
v124
=
sub_27E724(
5713
);
v125
=
3
;
v126
=
sub_26CE88;
v127
=
sub_27E724(
5730
);
v128
=
3
;
v129
=
sub_26CF3C;
v130
=
sub_27E724(
0x1678
);
v131
=
3
;
v132
=
sub_26CFF0;
v133
=
sub_27E724(
5768
);
v134
=
6
;
v135
=
sub_26D08C;
v136
=
sub_27E724(
5780
);
v137
=
6
;
v138
=
sub_26D1C8;
v139
=
sub_27E724(
5796
);
v140
=
7
;
v141
=
sub_26D334;
v142
=
sub_27E724(
5809
);
v143
=
7
;
v144
=
sub_26D33C;
v145
=
sub_27E724(
6915
);
v146
=
2
;
v147
=
sub_26D344;
v148
=
sub_27E724(
5826
);
v149
=
2
;
v150
=
sub_26D3B8;
v151
=
sub_27E724(
5840
);
v152
=
2
;
v153
=
sub_26D3E8;
v154
=
sub_27E724(
5858
);
v155
=
1
;
v156
=
sub_26DA50;
v157
=
sub_27E724(
5870
);
v158
=
1
;
v159
=
sub_26DA5C;
v160
=
sub_27E724(
5882
);
v161
=
7
;
v162
=
sub_26DC8C;
v163
=
sub_27E724(
5897
);
v164
=
7
;
v165
=
sub_26DC94;
v166
=
sub_27E724(
5916
);
v167
=
3
;
v168
=
sub_26DC9C;
v169
=
sub_27E724(
6460
);
v170
=
3
;
v171
=
sub_26DCB8;
v172
=
sub_27E724(
6669
);
v173
=
1
;
v174
=
sub_26C598;
v175
=
sub_27E724(
5934
);
v176
=
15
;
v177
=
sub_26C5C4;
v178
=
sub_27E724(
5949
);
v179
=
7
;
v180
=
sub_26E1B0;
v181
=
sub_27E724(
5974
);
v182
=
7
;
v183
=
sub_26E1B8;
v184
=
sub_27E724(
6003
);
v185
=
1
;
v186
=
sub_26C5B4;
v187
=
sub_27E724(
6012
);
v188
=
1
;
v189
=
sub_26C5BC;
v190
=
sub_27E724(
6021
);
v191
=
15
;
v192
=
sub_26C5DC;
v193
=
sub_27E724(
6032
);
v194
=
15
;
v195
=
sub_26C660;
v196
=
sub_27E724(
6042
);
v197
=
14
;
v198
=
sub_26C6E4;
v199
=
sub_27E724(
6058
);
v200
=
3
;
v201
=
sub_26C780;
v202
=
sub_27E724(
6388
);
v203
=
3
;
v204
=
sub_26C7D4;
v205
=
sub_27E724(
6074
);
v206
=
15
;
v207
=
sub_26D418;
v208
=
sub_27E724(
6085
);
v209
=
5
;
v210
=
sub_26D5AC;
v211
=
sub_27E724(
6098
);
v212
=
5
;
v213
=
sub_26D5EC;
v214
=
sub_27E724(
6115
);
v215
=
5
;
v216
=
sub_26D62C;
v217
=
sub_27E724(
6129
);
v218
=
5
;
v219
=
sub_26D704;
v220
=
sub_27E724(
6143
);
v221
=
5
;
v222
=
sub_26D6C0;
v223
=
sub_27E724(
6157
);
v224
=
3
;
v225
=
sub_26D748;
v226
=
sub_27E724(
6175
);
v227
=
5
;
v228
=
sub_26D870;
v229
=
sub_27E724(
6194
);
v230
=
5
;
v231
=
sub_26D8B0;
v232
=
sub_27E724(
6368
);
v233
=
1
;
v234
=
sub_26E1C0;
v235
=
sub_27E724(
6378
);
v236
=
2
;
v237
=
&sub_26E1D8;
v238
=
sub_27E724(
6482
);
v239
=
1
;
v240
=
sub_26DE88;
v241
=
sub_27E724(
6506
);
v242
=
3
;
v243
=
sub_26E264;
v244
=
sub_27E724(
6533
);
v245
=
2
;
v246
=
&sub_26E360;
v247
=
sub_27E724(
6561
);
v248
=
2
;
v249
=
&sub_26E3C8;
v250
=
sub_27E724(
6590
);
v251
=
1
;
v252
=
sub_26E430;
v253
=
sub_27E724(
6604
);
v254
=
1
;
v255
=
sub_26E438;
v256
=
sub_27E724(
6628
);
v257
=
1
;
v258
=
sub_26E450;
v259
=
sub_27E724(
6647
);
v260
=
2
;
v261
=
sub_26E46C;
v262
=
sub_27E724(
6783
);
v263
=
1
;
v264
=
sub_26E538;
v265
=
sub_27E724(
6802
);
v266
=
3
;
v267
=
&sub_26E540;
v268
=
sub_27E724(
6823
);
v269
=
1
;
v270
=
sub_26E5BC;
v271
=
sub_27E724(
6274
);
v272
=
5
;
v273
=
sub_26C828;
v274
=
sub_27E724(
6292
);
v275
=
1
;
v276
=
sub_26C8C4;
v277
=
sub_27E724(
6302
);
v278
=
1
;
v279
=
sub_26C8E0;
v280
=
sub_27E724(
6312
);
v281
=
3
;
v282
=
sub_26C8FC;
v283
=
sub_27E724(
6326
);
v284
=
3
;
v285
=
sub_26C97C;
v286
=
sub_27E724(
6340
);
v287
=
4
;
v288
=
sub_26CA00;
v289
=
sub_27E724(
6929
);
v290
=
3
;
v291
=
sub_26CA44;
v292
=
sub_27E724(
6939
);
v293
=
3
;
v294
=
sub_26CAC4;
v295
=
sub_27E724(
6949
);
v296
=
4
;
v297
=
sub_26CB48;
v298
=
sub_27E724(
6357
);
v299
=
2
;
v300
=
&sub_26CB90;
v301
=
sub_27E724(
6405
);
v302
=
3
;
v303
=
sub_26DD1C;
v304
=
sub_27E724(
6428
);
v305
=
3
;
v306
=
sub_26DD7C;
v307
=
sub_27E724(
6442
);
v308
=
3
;
v309
=
sub_26DE00;
v310
=
sub_27E724(
6695
);
v311
=
1
;
v312
=
sub_26DE08;
v313
=
sub_27E724(
6714
);
v314
=
1
;
v315
=
sub_26DE38;
v316
=
sub_27E724(
6733
);
v317
=
1
;
v318
=
sub_26DE68;
v319
=
sub_27E724(
6766
);
v320
=
1
;
v321
=
sub_26DE84;
v322
=
sub_27E724(
6836
);
v323
=
3
;
v324
=
&sub_26DF54;
v325
=
sub_27E724(
6851
);
v326
=
4
;
v327
=
&sub_26DFBC;
v328
=
sub_27E724(
6962
);
v329
=
14
;
v330
=
sub_26E044;
v331
=
sub_27E724(
6978
);
v332
=
5
;
v2
=
0LL
;
v333
=
sub_26E058;
do
{
v3
=
*
(unsigned __int8
*
*
)((char
*
)&v11
+
v2
*
8
);
v4
=
strlen_sub_2398FC((__int64)v3);
v5
=
crc32_sub_22B670(v3, v4);
v6
=
v13[v2];
v7
=
*
(_OWORD
*
)((char
*
)&v11
+
v2
*
8
);
v8
=
v5;
v10
=
v6;
v9
=
v7;
result
=
sub_26B030(v1, &v8);
v2
+
=
3LL
;
}
while
( v2 !
=
324
);
}
return
result;
}
|
- 在方法
sub_268F9C对自定义的脚本进行语法解析,如果是方法,找到对应的模拟方法的Hander,计算方法名crc,通过crc查找上面表中对应的方法地址并执行
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
sub_268F9C onEnter:
0
1
2
3
4
5
6
7
8
9
A B C D E F
0123456789ABCDEF
b400007137d6b058
6d
6f
64
75
6c
65
5f
65
78
69
73
74
73
28
22
6c
module_exists("l
b400007137d6b068
69
62
68
6f
75
64
69
6e
69
5f
34
31
35
63
2e
73
ibhoudini_415c.s
b400007137d6b078
6f
22
29
00
00
00
00
00
00
00
00
00
00
00
00
00
o").............
b400007137d6b088
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b098
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b0a8
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b0b8
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b0c8
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b0d8
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b0e8
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b0f8
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b108
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b118
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b128
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b138
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
b400007137d6b148
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
00
................
|
- 在方法
sub_22B670对代码段做了crc校验
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
libtersafe2 base:
0x753bc01000
sub_22B670 onEnter:
0
1
2
3
4
5
6
7
8
9
A B C D E F
0123456789ABCDEF
753bc27000
1f
28
00
71
20
04
00
54
7f
04
00
f1
61
00
00
54
.(.q ..T....a..T
753bc27010
1f
28
00
71
ad
03
00
54
7f
04
00
f1 f3 d7
9f
1a
.(.q...T........
753bc27020
53
00
00
35
23
03
00
b5
1f
50
00
71
13
00
80
52
S..
5
#....P.q...R
753bc27030
c0
02
00
54
e0
03
01
aa
61
1b
00
f0
21
e0
26
91
...T....a...!.&.
753bc27040
f5
03
02
aa
86
7a
0a
94
00
01
00
b4
61
1b
00
f0 .....z......a...
753bc27050
62
1b
00
f0
21
00
27
91
42
20
27
91
7e
4c
0a
94
b...!.
'.B '
.~L..
753bc27060
80
02
02
39
09
00
00
14
61
1b
00
f0 e0
03
15
aa ...
9.
...a.......
753bc27070
21
60
27
91
7a
4b
0a
94
f3
03
00
2a
60
00
00
35
!`'.zK.....
*
`..
5
753bc27080
20
00
80
52
80
02
02
39
e0
03
13
2a
f5
13
40
f9 ..R...
9.
..
*
..@.
753bc27090
f3
53
41
a9 fd
7b
c3 a8 c0
03
5f
d6
1f
08
40
71
.SA..{...._...@q
753bc270a0
00
0b
00
54
08
05
00
54
1f
00
01
71
e1
03
00
2a
...T...T...q...
*
753bc270b0
20
0c
00
54
48
02
00
54
1f
10
00
71
a0
09
00
54
..TH..T...q...T
753bc270c0
c8
00
00
54
00
04
00
51
21
00
80
52
1f
04
00
71
...T...Q!..R...q
753bc270d0
29
0b
00
54
57
00
00
14
1f
40
00
71
01
02
80
52
)..TW....@.q...R
753bc270e0
a0
0a
00
54
1f
80
00
71
01
04
80
52
40
0a
00
54
...T...q...R@..T
753bc270f0
1f
20
00
71
e1
09
00
54
3e
00
00
14
1f
00
08
71
. .q...T>......q
0x340000
|
- 在方法
sub_22B6AC对代码段每0x1000大小做一次crc校验
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
|
libtersafe2 base:
0x753bc01000
sub_22B6AC onEnter:
0
1
2
3
4
5
6
7
8
9
A B C D E F
0123456789ABCDEF
753bc27000
1f
28
00
71
20
04
00
54
7f
04
00
f1
61
00
00
54
.(.q ..T....a..T
753bc27010
1f
28
00
71
ad
03
00
54
7f
04
00
f1 f3 d7
9f
1a
.(.q...T........
753bc27020
53
00
00
35
23
03
00
b5
1f
50
00
71
13
00
80
52
S..
5
#....P.q...R
753bc27030
c0
02
00
54
e0
03
01
aa
61
1b
00
f0
21
e0
26
91
...T....a...!.&.
753bc27040
f5
03
02
aa
86
7a
0a
94
00
01
00
b4
61
1b
00
f0 .....z......a...
753bc27050
62
1b
00
f0
21
00
27
91
42
20
27
91
7e
4c
0a
94
b...!.
'.B '
.~L..
753bc27060
80
02
02
39
09
00
00
14
61
1b
00
f0 e0
03
15
aa ...
9.
...a.......
753bc27070
21
60
27
91
7a
4b
0a
94
f3
03
00
2a
60
00
00
35
!`'.zK.....
*
`..
5
753bc27080
20
00
80
52
80
02
02
39
e0
03
13
2a
f5
13
40
f9 ..R...
9.
..
*
..@.
753bc27090
f3
53
41
a9 fd
7b
c3 a8 c0
03
5f
d6
1f
08
40
71
.SA..{...._...@q
753bc270a0
00
0b
00
54
08
05
00
54
1f
00
01
71
e1
03
00
2a
...T...T...q...
*
753bc270b0
20
0c
00
54
48
02
00
54
1f
10
00
71
a0
09
00
54
..TH..T...q...T
753bc270c0
c8
00
00
54
00
04
00
51
21
00
80
52
1f
04
00
71
...T...Q!..R...q
753bc270d0
29
0b
00
54
57
00
00
14
1f
40
00
71
01
02
80
52
)..TW....@.q...R
753bc270e0
a0
0a
00
54
1f
80
00
71
01
04
80
52
40
0a
00
54
...T...q...R@..T
753bc270f0
1f
20
00
71
e1
09
00
54
3e
00
00
14
1f
00
08
71
. .q...T>......q
0x1000
0xffffffff
sub_22B6AC onEnter:
0xa92ef9dc
sub_22B6AC onEnter:
0
1
2
3
4
5
6
7
8
9
A B C D E F
0123456789ABCDEF
753bc28000
ff
83
00
d1 fd
7b
01
a9 fd
43
00
91
c8
24
00
f0 .....{...C...$..
753bc28010
00
41
22
91
47
7a
02
94
c8
23
00
f0
08
e9
47
f9 .A".Gz...
#....G.
753bc28020
c0
24
00
f0
01
40
22
91
e0
23
00
90
02
f4
43
f9 .$...@"..
#....C.
753bc28030
e0
03
08
aa b7 f7 ff
97
a0 c3
1f
b8 fd
7b
41
a9 .............{A.
753bc28040
ff
83
00
91
c0
03
5f
d6 ff
83
00
d1 fd
7b
01
a9 ......_......{..
753bc28050
fd
43
00
91
c8
24
00
f0
00
01
23
91
35
7a
02
94
.C...$....
#.5z..
753bc28060
c8
23
00
f0
08
e9
47
f9 c0
24
00
f0
01
00
23
91
.
#....G..$....#.
753bc28070
e0
23
00
90
02
f4
43
f9 e0
03
08
aa a5 f7 ff
97
.
#....C.........
753bc28080
a0 c3
1f
b8 fd
7b
41
a9 ff
83
00
91
c0
03
5f
d6 .....{A......._.
753bc28090
ff
83
00
d1 fd
7b
01
a9 fd
43
00
91
c8
24
00
f0 .....{...C...$..
753bc280a0
00
c1
23
91
23
7a
02
94
c8
23
00
f0
08
e9
47
f9 ..
#.#z...#....G.
753bc280b0
c0
24
00
f0
01
c0
23
91
e0
23
00
90
02
f4
43
f9 .$....
#..#....C.
753bc280c0
e0
03
08
aa
93
f7 ff
97
a0 c3
1f
b8 fd
7b
41
a9 .............{A.
753bc280d0
ff
83
00
91
c0
03
5f
d6 ff
83
00
d1 fd
7b
01
a9 ......_......{..
753bc280e0
fd
43
00
91
c8
24
00
f0
00
81
24
91
90
e6
01
94
.C...$....$.....
753bc280f0
e8
23
00
90
08
41
44
f9 c0
24
00
f0
00
80
24
91
.
#...AD..$....$. 0x1000 0xa92ef9dc
sub_22B6AC onEnter:
0x66073cb2
sub_22B6AC onEnter:
0
1
2
3
4
5
6
7
8
9
A B C D E F
0123456789ABCDEF
753bc29000
fd
43
00
91
f3
24
00
d0
73
02
11
91
e0
03
13
aa .C...$..s.......
753bc29010
dc
2d
08
94
c0
23
00
f0 c2
23
00
f0
00
c4
41
f9 .
-
...
#...#....A.
753bc29020
42
f4
43
f9 fd
7b
41
a9 e1
03
13
aa f3
07
42
f8 B.C..{A.......B.
753bc29030
b8 f3 ff
17
f3
0f
1e
f8 fd
7b
01
a9 fd
43
00
91
.........{...C..
753bc29040
f3
24
00
d0
73
42
26
91
e0
03
13
aa
89
2d
08
94
.$..sB&......
-
..
753bc29050
c0
23
00
f0 c2
23
00
f0
00
14
40
f9
42
f4
43
f9 .
#...#....@.B.C.
753bc29060
fd
7b
41
a9 e1
03
13
aa f3
07
42
f8 a9 f3 ff
17
.{A.......B.....
753bc29070
f3
0f
1e
f8 fd
7b
01
a9 fd
43
00
91
40
6a
81
52
.....{...C..@j.R
753bc29080
a9
59
09
94
13
25
00
b0
73
22
2a
91
60
02
00
f9 .Y...
%
..s"
*
.`...
753bc29090
21
e7
08
94
48
12
00
f0
08
b1
23
91
60
a2
00
a9 !...H.....
#.`...
753bc290a0
20
6b
81
52
a0
59
09
94
60
0e
00
f9
1c
e7
08
94
k.R.Y..`.......
753bc290b0
48
12
00
f0
08
21
28
91
60
22
02
a9 e0
6c
81
52
H....!(.`"...l.R
753bc290c0
99
59
09
94
60
1a
00
f9
17
e7
08
94
48
12
00
f0 .Y..`.......H...
753bc290d0
08
81
36
91
60
a2
03
a9 e0
6e
81
52
92
59
09
94
..
6.
`....n.R.Y..
753bc290e0
60
26
00
f9
12
e7
08
94
68
12
00
90
08
41
08
91
`&......h....A..
753bc290f0
60
22
05
a9 e0
70
81
52
8b
59
09
94
60
32
00
f9 `"...p.R.Y..`
2.
.
0x1000
0x66073cb2
sub_22B6AC onEnter:
0x30aa1225
|
- 其他的检测暂未细看
记得比较流水账,大佬们将就看。
更多【某手游xqtd的简单分析】相关视频教程:www.yxfzedu.com
相关文章推荐
- Pwn-2022长城杯决赛pwn - Android安全 CTF对抗 IOS安全
- 软件逆向-Wibu Codemeter 7.3学习笔记——Codemeter服务端 - Android安全 CTF对抗 IOS安全
- Pwn-沙箱逃逸之google ctf 2019 Monochromatic writeup - Android安全 CTF对抗 IOS安全
- 软件逆向-Wibu Codemeter 7.3学习笔记——AxProtector壳初探 - Android安全 CTF对抗 IOS安全
- 企业安全-学习Kubernetes笔记——暴露站点服务(Ingress) - Android安全 CTF对抗 IOS安全
- 企业安全-学习Kubernetes笔记——部署数据库站点(MySql) - Android安全 CTF对抗 IOS安全
- 企业安全-学习Kubernetes笔记——部署web站点环境(PHP+Nginx) - Android安全 CTF对抗 IOS安全
- 企业安全-学习Kubernetes笔记——安装NFS驱动 - Android安全 CTF对抗 IOS安全
- 企业安全-学习Kubernetes笔记——kubeadm安装Kubernetes - Android安全 CTF对抗 IOS安全
- 软件逆向-wibu软授权(四) - Android安全 CTF对抗 IOS安全
- 软件逆向-使用IDAPython开发复制RVA的插件 - Android安全 CTF对抗 IOS安全
- 2-wibu软授权(三) - Android安全 CTF对抗 IOS安全
- 软件逆向-wibu软授权(二) - Android安全 CTF对抗 IOS安全
- 软件逆向-wibu软授权(一) - Android安全 CTF对抗 IOS安全
- 软件逆向- PE格式:分析IatHook并实现 - Android安全 CTF对抗 IOS安全
- Android安全-安卓API自动化安全扫描 - Android安全 CTF对抗 IOS安全
- 二进制漏洞- Chrome v8 Issue 1307610漏洞及其利用分析 - Android安全 CTF对抗 IOS安全
- iOS安全-IOS 脱壳入坑经验分享 - Android安全 CTF对抗 IOS安全
- 二进制漏洞-Windows UAF 漏洞分析CVE-2014-4113 - Android安全 CTF对抗 IOS安全
- CTF对抗-lua 逆向学习 & RCTF picstore 还原代码块 - Android安全 CTF对抗 IOS安全
记录自己的技术轨迹
文章规则:
1):文章标题请尽量与文章内容相符
2):严禁色情、血腥、暴力
3):严禁发布任何形式的广告贴
4):严禁发表关于中国的政治类话题
5):严格遵守中国互联网法律法规
6):有侵权,疑问可发邮件至service@yxfzedu.com
近期原创 更多
www.yxfzedu.com是一个分享游戏安全,游戏外挂与反外挂,游戏驱动保护的视频网站!
接各种驱动定制如:游戏读写驱动,软件内存保护,防止调试等功能定制。
出租读写驱动,调试驱动,无痕注入支持各种游戏。
邮箱:service@yxfzedu.com
QQ:851920120
特别说明:不接游戏数据分析,外挂编写,登陆协议等类似业务。
接各种驱动定制如:游戏读写驱动,软件内存保护,防止调试等功能定制。
出租读写驱动,调试驱动,无痕注入支持各种游戏。
邮箱:service@yxfzedu.com
QQ:851920120
特别说明:不接游戏数据分析,外挂编写,登陆协议等类似业务。
